Remote working, Cybersecurity, Management and COVID-19: be more attentive than ever and stick to best practices!
The current crisis and containment situation we are experiencing is generating a flood of stress and anxiety. This may have a negative impact on our professional exchanges and increase our vulnerability to cyber-attacks. There is a real risk that the hindsight and critical thinking we usually display in terms of good cyber practices could be neglected in such circumstances.
This new digital environment offers a multitude of opportunities for professional hackers:
- Fake president scams,
- viruses,
- phishing,
- ransomware,
- social engineering in the field of information security,
… many examples of psychological hacking for scamming purposes will arise during this containment period.
Social distancing has a huge impact on our daily work habits, our interactions with colleagues and suppliers and thus inevitably on the exchanges of data that now go with all of this.
It is this paradigm shift that creates vulnerability and creates an increased risk of exposure, exfiltration or even the destruction of sensitive data for the company.
In this particular context, management must remind employees about the rules of good business practices they need to respect in order to ensure a high level of security, in actual fact it needs to be almost equivalent to that of the office.
Cyberspace has become our new open workspace. Today more than ever, it is all the more important to remind employees about the basic good practices for “teleworking” in complete security.
Let’s focus today on social engineering and fake president scams, we will deal with the topics of phishing and ransomware in a future article
Social engineering and fake president scams
The risks of identity theft, fake president fraud and bank transfer fraud increase considerably during a crisis such as the present one. It is important to raise awareness among teleworking employees and warn them that they are becoming prime targets for hackers.
Be careful, the caller or the sender of the e-mail you receive may not be who they claim to be!
1. The objective
To usurp the identity of a client in order to require an employee to make a fraudulent transfer, using the pretext of urgency and confidentiality.
By pretending to be a senior manager of the company, the fraudster puts the employee in a position of hierarchical subordination. Thanks to this position of strength in the relationship, the fraudster has powerful leverage to manipulate his/her victim.
(S)He then uses the authority that (s)he claims to have, “I’m giving you an order here”, whilst also making the employee feel valued by adding “I am relying on you”.
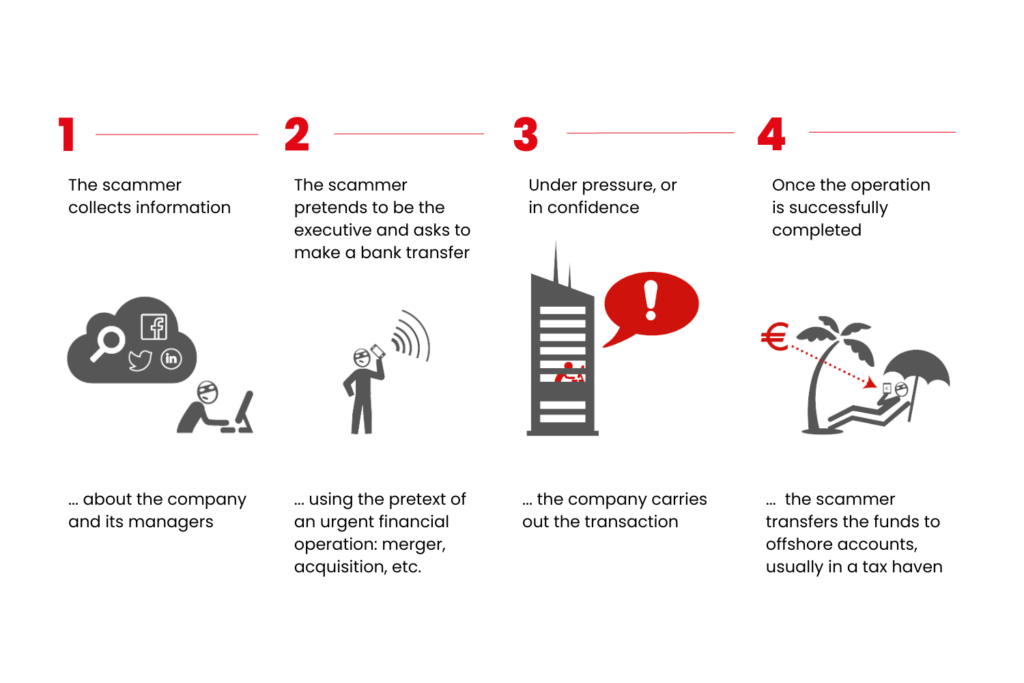
2. The process
How the fake president fraud rolled out?
3. The right reflexes
What should you do when faced with an unusual request?
Let us help you!
Our partner

WANT TO RECEIVE OUR LATEST THOUGHT LEADERSHIP CONTENT?
Related posts
 Take the Guesswork out of People Management
Take the Guesswork out of People Management
 From processes to people: achieving quality
From processes to people: achieving quality
 Daring to lead Positive Transformation: What if Positive Emotional Capital was your key to sustainable change?
Daring to lead Positive Transformation: What if Positive Emotional Capital was your key to sustainable change?
 Why hire Change management professionals? We can do it alone!
Why hire Change management professionals? We can do it alone!
 Digital Transformation and Change Management: Lessons shared in an event hosted by Cebi and MindForest
Digital Transformation and Change Management: Lessons shared in an event hosted by Cebi and MindForest